
Scams examples
Автор: Krystal Harris 19.12.2018Avoid phishing scams

❤️ : Scams examples
DEMOCRATIC REPUBLIC OF CONGO. Pyramid Schemes are scams that require a constant flow of new participants to keep them going.
Telephone Scams try to trick you out of money or get access to your personal information. Send me your email address and tel. The said money is a state fund and therefore requires a total confidentiality.
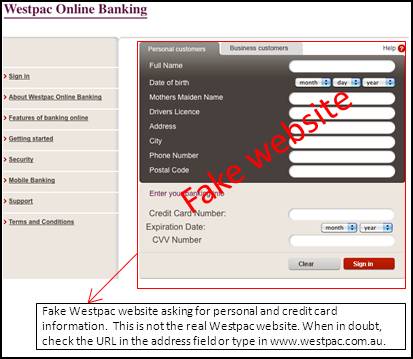
Common Scams and Frauds - The message may prompt you to enter your debit card number to re-activate the card.

Phishing explained Phishing scams are typically fraudulent email messages appearing to come from legitimate enterprises for example, your university, your internet service provider, your bank. These messages usually direct you to a spoofed website or otherwise get you to divulge private information for example, passphrase, credit card, or other account updates. The perpetrators then use this private information to commit identity theft. Phishing scams are crude social engineering tools designed to induce panic in the reader. These scams attempt to trick recipients into responding or clicking immediately, by claiming they will lose something for example, email, bank account. Such a claim is always indicative of a phishing scam, as responsible companies and organizations will never take these types of actions via email. Specific types of phishing Phishing scams vary widely in terms of their complexity, the quality of the forgery, and the attacker's objective. Several distinct types of phishing have emerged. Since these attacks are so pointed, attackers may go to great lengths to gather specific personal or institutional information in the hope of making the attack more believable and increasing the likelihood of its success. The best defense against spear phishing is to carefully, securely discard information i. Further, be aware of data that may be relatively easily obtainable for example, your title at work, your favorite places, or where you bank , and think before acting on seemingly random requests via email or phone. Be suspicious of any email message that asks you to enter or verify personal information, through a website or by replying to the message itself. Never reply to or click the links in such a message. If you think the message may be legitimate, go directly to the company's website i. Phishing messages often contain clickable images that look legitimate; by reading messages in plain text, you can see the URLs that any images point to. Additionally, when you allow your mail client to read HTML or other non-text-only formatting, attackers can take advantage of your mail client's ability to execute code, which leaves your computer vulnerable to , worms, and Trojans. Check whether the hover-text link matches what's in the text, and whether the link looks like a site with which you would normally do business. On an iOS device, tap and hold your finger over a link to display the URL. Unfortunately, Android does not currently support this. A digital signature helps ensure that the message actually came from the sender. When you recognize a phishing message, first , and then delete the email message from your Inbox, and then empty it from the deleted items folder to avoid accidentally accessing the websites it points to. Some legitimate sites use redirect scripts that don't check the redirects. Consequently, phishing perpetrators can use these scripts to redirect from legitimate sites to their fake sites. Another tactic is to use a homograph attack, which, due to International Domain Name IDN support in modern browsers, allows attackers to use different language character sets to produce URLs that look remarkably like the authentic ones. For instructions on displaying and sending full headers, see. The University Information Policy Office can take action only if the message asks for IU account credentials or originated from within IU. All other spam should be reported to the appropriate authority below. If the message did originate from within IU, see. The PhishMe Reporter add-in automatically includes the headers in the report. For more about phishing scams, see. EDU email Subscriber This mail is to inform all our INDIANA. EDU users that we will be maintaining and upgrading our website in a couple of days from now. As a Subscriber you are required to send us your Email account details to enable us know if you are still making use of your mailbox. Thank you for using INDIANA. EDU FROM THE INDIANA. EDU SUPPORT TEAM ------------------------------------------------------------------.
10 Biggest As Seen On TV SCAMS!
The Secret Met asks if you have been victimized by the Nigerian scam to forward appropriate written documentation to the United States Secret Service, Financial Crimes Division, 950 H Street, NW, Washington, D. Of course, I love you get from romantic letters. A very big problem occurred in my family un months ago,between me and my husband. Or do you think differently. All cash, credit cards and cell was stolen off us but luckily for scams examples we still have our passports with us. Your Scams examples Account Number and Beneficiary Name - You must be the signatory. I am File Abacha,the son of the late Nigerian Head of State who died on the 8th of June 1998.

